A California hacker who has become an expert in cracking locks has invented a 3D-printed machine that can crack a rotary combination lock in around 30 seconds – and he's released the plans, 3D models, and code as open source.
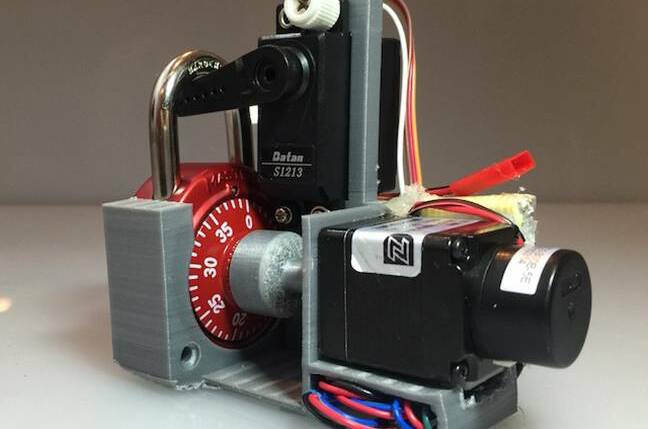
A few weeks ago, Samy Kamkar told the world about a manufacturing flaw in Master Lock combination locks that reveals the combination by measuring how the dial interacts with the shackle. It's a moderately tricky thing to do, requiring some software, so now he's mechanized the process with the Combo Breaker device.
The Combo Breaker uses a stepper motor to rotate the Master Lock combination dial, a servo motor to try and open the mechanism, an Arduino chip to run the software, and 3D printed parts to house the lock and ensure a firm fit with the dial controller.
If you merely slip a Master Lock into the device and set it running, the Combo Breaker will take about five minutes to find the combination – which is worrying, but not very useful if you're trying to, for example, break into someone's high school or gym locker.
But if you use Kamkar's earlier method to "prime" the device by finding the first digit of the combination by hand – something that's relatively easy to do – then the Combo Breaker can do the job in 30 seconds or less. That's quick enough to be a serious problem in the right circumstances (and the wrong hands).
Before you start panicking, Kamkar tested the device on a cheaper version of the Master Lock combination dial mechanism. The company makes tougher rotary combo locks and the Combo Breaker isn't guaranteed to work on all of them.
This isn't not the first time Kamkar has caused a ruckus; he's been a major disruptive force in the tech industry for a while now. At 18, he co-founded Fonality, a multimillion dollar communications company, but then got seriously into hacking.
When he was 20, Kamkar created the Samy worm and released it onto MySpace, forcing the site to shut down temporarily. The worm was one of the fastest-spreading in history, and although it didn't carry a malicious payload, it still earned him a visit from US law enforcement and a felony charge of computer hacking.
Since then he's demonstrated critical weaknesses in near-field communications and RFID chips, discovered a major flaw in PHP, and learned how to hijack drones in mid-flight. He's a regular at the hacking conference circuit and is now an independent security consultant.
No comments:
Post a Comment